Device control is a critical yet often overlooked layer of defense in modern cybersecurity. It closes gaps that many security programs leave wide open, helping organizations prevent malware infections, stop unauthorized access, and gain deep visibility into how physical hardware interacts with their network. In fact, nearly one in four organizations report detecting unauthorized hardware on their networks every month. Almost half have experienced a breach tied to unmanaged endpoints. These numbers make one thing clear: device control is not optional, it is foundational.
What Is Device Control and Why It Matters
At its core, device control is the ability to manage, monitor, and restrict physical device connections to corporate endpoints. This includes USB drives, printers, Bluetooth accessories, and external storage media. With device control in place, security teams decide which devices to permit, block, or handle with special rules. This control makes it significantly easier to prevent data loss, block malicious software, and enforce internal data governance policies.
Consider the implications of leaving this unchecked. Without guardrails, anyone can plug in a USB drive, potentially introducing malware or siphoning off confidential data. With remote work and bring-your-own-device trends continuing to rise, the threat surface has expanded far beyond the traditional office perimeter. Device control gives organizations a way to reestablish trust and control, no matter where their endpoints are.
Common Risks Without Device Control
Organizations without device control are vulnerable to multiple attack vectors and operational threats. Examples include:
- Malware infections delivered through USB devices or rogue peripherals
- Insider threats where employees exfiltrate sensitive data using removable storage
- Shadow IT devices introducing unknown risks in bring-your-own-device (BYOD) environments
- Organizations often lack visibility into the physical devices connected to their corporate hardware.
These risks are especially critical in regulated industries or in distributed workforces with inconsistent device hygiene.
How Device Control Strengthens Endpoint Detection and Response
Endpoint Detection and Response (EDR) platforms are designed to monitor, detect, and respond to threats across endpoint devices. While traditional antivirus tools rely on signature-based detection, EDR focuses on behavior. It analyzes patterns and triggers alerts or automated responses, such as quarantining suspicious files or isolating compromised devices.
By integrating device control into EDR, security teams can centrally manage and enforce rules around physical hardware in real time. This not only strengthens an organization’s security posture but also allows for faster containment of potential threats. For example, if an unknown USB is inserted into a company laptop, device control policies within the EDR platform can immediately block access, trigger an alert, and log the event for further analysis.
Why Device Control Belongs in Every Endpoint Security Strategy
Properly implementing device control delivers immediate benefits. First, it dramatically reduces one of the most common malware delivery methods: removable storage. By disabling or limiting USB access, organizations cut off an entire category of initial attack vectors. It also acts as a strong deterrent against insider threats. Preventing write access to external drives or requiring encryption for data transfers helps protect sensitive information from being leaked, either accidentally or intentionally. From a compliance perspective, device control helps meet the requirements of data protection frameworks like GDPR, HIPAA, and PCI DSS. Enforcing strict policies on data access and maintaining detailed logs simplifies auditing and reinforces corporate accountability. Moreover, it boosts visibility. Security teams monitor which devices connect, when they connect, and who connects them in real time.. This intelligence is invaluable for incident response, forensic analysis, and ongoing risk assessments. Especially in hybrid work environments, this visibility helps eliminate blind spots that attackers might otherwise exploit.
Smart Implementation: Turning Strategy into Action
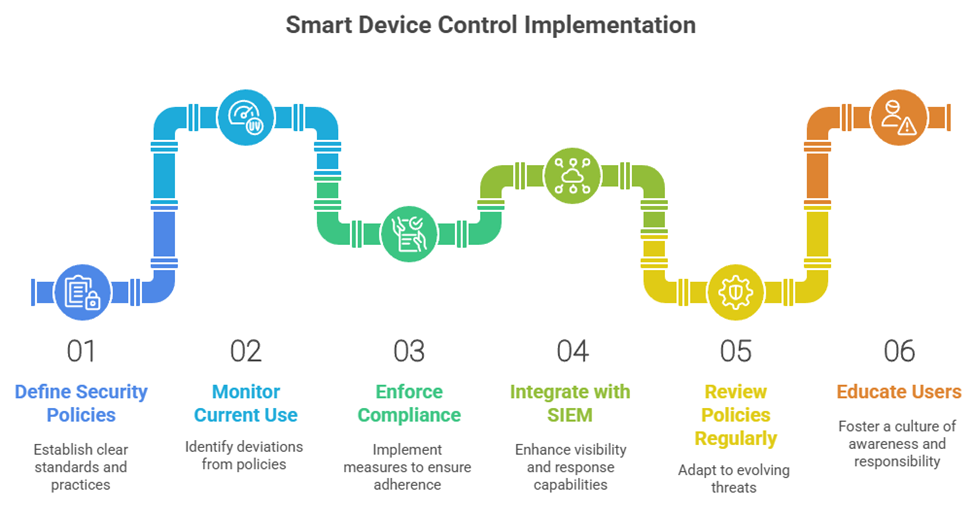
Deploying device control is not just a technical challenge. It requires a clear, strategic approach that takes organizational dynamics into account. Start by defining device usage policies that are tailored to specific roles, departments, and geographical locations. What makes sense for the marketing team may not work for engineering.
Before moving to full enforcement, use monitoring mode to understand existing behavior. This baseline insight helps uncover legitimate business needs while preventing unnecessary disruption when policies are rolled out.
Next, integrate device control telemetry into your broader security operations. Feed event data into your Security Information and Event Management (SIEM) system, correlate it with other indicators, and set up automated responses where possible.
Policy management is not a one-time event. Regularly review and refine your rules as new devices and workflows emerge. Define a clear process to manage exceptions, and document, justify, and monitor all approvals.
Finally, invest in user education. Make sure employees understand why these controls are in place, what the acceptable behaviors are, and what secure alternatives exist. A well-informed workforce is one of the most effective tools in preventing policy circumvention.
Strategic Steps for Security Leaders
Start by assessing whether your current EDR solution includes built-in device control capabilities. Conduct a thorough audit of how devices are currently being used across your endpoints. Use that data to craft a phased rollout plan that begins with visibility and transitions into enforcement. Define a process for managing hardware exceptions. Set up your SIEM and threat detection pipelines to ingest and analyze device control data. Make it part of your broader threat intelligence and response strategy. Most importantly, stop thinking of device control as a standalone tool. It is a critical part of your endpoint defense architecture, providing both tactical benefits and long-term strategic value.
Conclusion
Device control is not just a nice-to-have feature. It is a foundational element of any strong endpoint security strategy. When integrated with EDR, it equips organizations with the tools to proactively block attacks, protect sensitive data, and gain meaningful insight into device-level activity. If you need help developing device control policies, conducting a risk assessment, or evaluating EDR solutions that include this capability, contact the experts at Breach Point.







